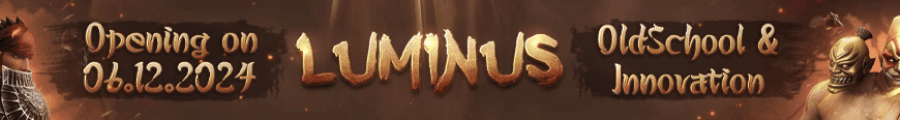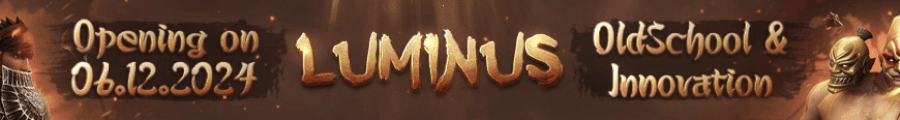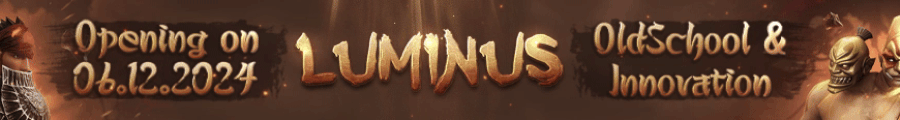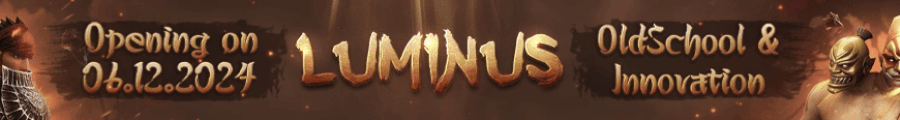Hier schonmal etwas das ich bisschen rausgefunden habe ![]()
Hosts :
127.0.0.1 metin2.nprotect.gameforge.com
127.0.0.1 patch.metin2.denote
127.0.0.1 52.79.132.29
127.0.0.1 mgr.gameguard.co.kr
127.0.0.1 gameguard.gfsrv.net
Weiteres kommt sobald ich mehr habe ![]()
Aber das ist einfach schonmal wichtig wenn man einen Debugger attachen möchte ![]()
Edit :
ZitatAlles anzeigenAddress Message
Themida - Winlicense Ultra Unpacker 1.0
-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
03030021 Breakpoint at 03030021
03030028 Breakpoint at 03030028
42.197 MB +/-
42.734 MB +/-
PE HEADER: 400000 | 1000
CODESECTION: 401000 | 11F0000
PE HEADER till CODESECTION Distance: 1000Value of 1000 = Normal!
Your Target seems to be a normal file!
Unpacking of NET targets is diffrent!
Dump running process with WinHex and then fix the whole PE and NET struct!
006FE56B Breakpoint at metin2cl.006FE56B
006FE56D Breakpoint at metin2cl.006FE56D
Windows 7 or higher found!
Newer SetEvent & Kernel32 ADs Redirecting in Realtime is disabled by user!
Kernel Ex Table Start: 76530338
04D2003F Breakpoint at 04D2003F
PE DUMPSEC: VA 4D30000 - VS 2C000
PE ANTISEC: VA 4D31000
PE OEPMAKE: VA 4D31600
SETEVENT_VM: VA 4D321D0
PE I-Table: VA 4D33000
VP - STORE: VA 4D32F00
and or...
API JUMP-T: VA 4D33000
04D2003F Breakpoint at 04D2003F
RISC VM Store Section VA is: 4ED0000 - VS 200000
04D20041 Breakpoint at 04D20041
77CDE42A Hardware breakpoint 1 at ntdll.77CDE42A
Found WL Intern Export API Access at: 77CDE4B6
Use this address to get all intern access WL APIs!
Es handelt sich um eine Themida+WinLicense Protection!